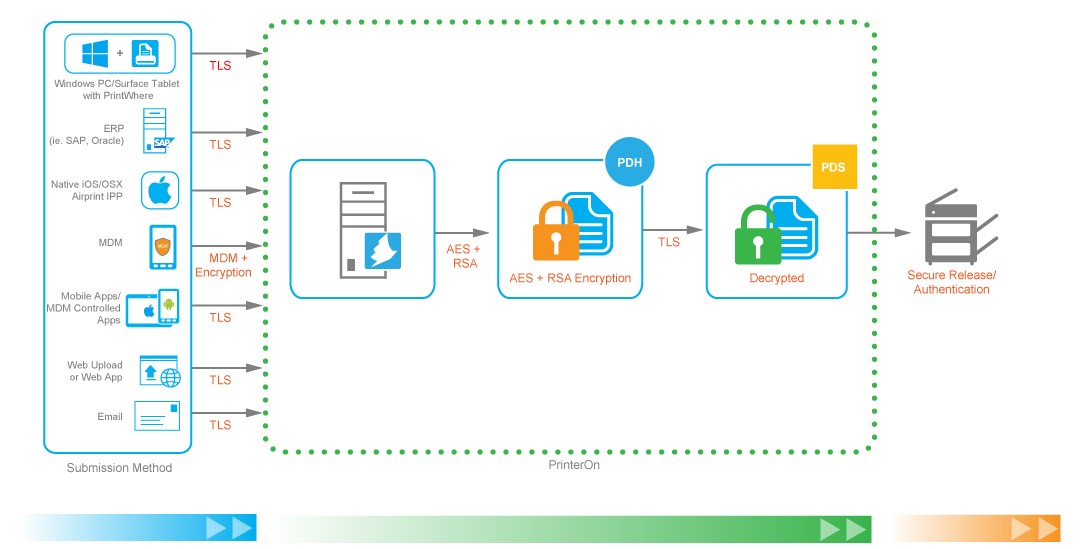
Network Security
To provide secure, enterprise cloud printing, PrinterOn leverages multiple methods of network security to make sure printing is always done in a secure manner no matter who is using the service or where they are accessing it from.
PrinterOn applies industry standard best practices for all network security and communications. All PrinterOn services are protected by fully signed and verifiable certificates that ensure connections are encrypted and that their authenticity can be confirmed. Additionally, clients such as the PrinterOn mobile apps, ensure that all communication is done securely at the client level. Users will be notified whenever attempting to connect to any discovered services using a self-signed certificate to ensure users are aware of the service identity prior to a connection being established.